SFTP Protocol: A Secure Way to Transfer Files
SFTP protocol: what is it?
The Internet is an environment whose main purpose is to transfer information. It can be entertaining, personal, commercial, confidential, the disclosure of which to third parties is unacceptable, fraught with serious financial and reputational losses.
This situation can be excluded by using special data transfer protocols that support encryption technologies that provide protection against interception, theft, intentional damage and distortion. A typical example is the SFTP protocol. What are its features? What are the advantages and differences from alternatives?
A little history
The predecessor of the SFTP protocol is FTP, the history of which begins in 1971. It successfully handled its main task, the transfer of information, however, the exchange was conducted in an open form, when intercepted, all data was immediately visible to the attacker, decryption was not required.
The Internet was developing, the number of users was growing exponentially, the basic set of functions was expanding, the commercial sphere was actively covered, involving interaction with confidential data, bank details. Of course, the transfer of such information over an unprotected channel could have catastrophic consequences.
The problem was solved by combining the FTP protocol and SSL, which supports encryption algorithms. The abbreviation FTPS began to be used to denote the new development, and a little later its modified version, SFTP, appeared.
General concept
Explanation of the abbreviation SFTP - “Secure File Transfer Protocol”. The technology provides fast, secure data exchange, allows you to confidently interact with both large and small volumes. The most important advantage of the protocol is ensuring protection at all stages of transfer, which leaves no chance for intruders.
To use SFTP, you must first install the appropriate client, which has all the functions, from deleting information to moving it between directories, physical, virtual devices.
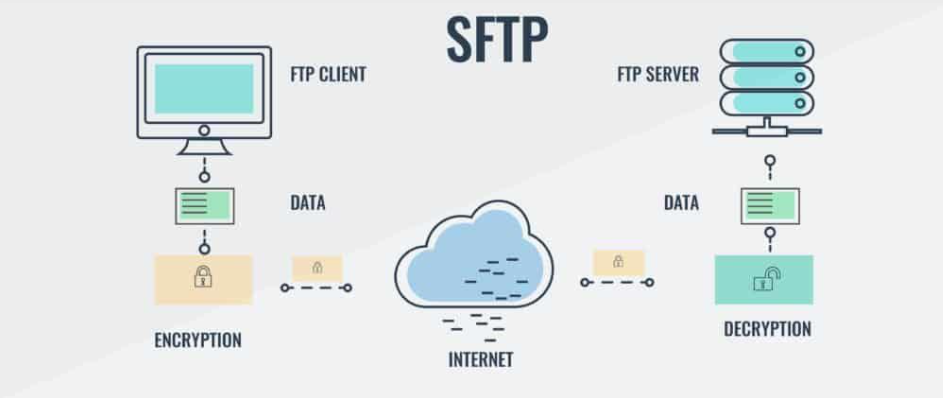
The transfer scheme can be represented as follows:
- Connection. The user's computer establishes a connection with the server.
- Authorization. The authenticity of the account is checked, if necessary, a password is entered, a full-fledged communication session begins.
- Transfer. Files are sent from the server to the computer, or in the opposite direction. In the process, they are encrypted, which guarantees security. The encryption algorithm installed by default is RSA, if necessary, it can be changed.
- End of session. Previously used resources are released.
Who needs it?
The following departments, organizations, and structures actively use the SFTP protocol:
- Large enterprises. The idea is to securely transfer data between departments, representative offices, including those located in different cities and countries.
- Web hosting. SFTP helps to safely place a website, application, program on the server, regardless of hardware requirements, specifics, and scale.
- Banks, financial institutions. The protocol allows you to transfer personal data of clients, account details without unnecessary risks.
- Companies specializing in software development, regardless of the specifics. SFTP is well suited for fast transfer of large files that form the basis of source code.

Advantages
If you compare SFTP with its predecessor, FTP, its following strengths become obvious:
- Maximum level of information security. The modern protocol encrypts the entire session. Even if intruders manage to intercept the data, they will not gain any benefit from this, they will not be able to decode it.
- Reliability of authorization. SFTP uses public keys that help the system clearly recognize the user. The risk of unauthorized access is minimal, as well as compromise, intentional change of information.
- Preservation of information integrity. SFTP algorithms ensure that all packets maintain integrity, their transmission is not associated with errors and failures, they reach the addressee unchanged, can be accurately identified.
- Ease of use. The interface of most programs that allow you to use SFTP is intuitive, even users who have no similar experience and minimal computer literacy will be able to use all the functions and establish effective data exchange.
- Universality. SFTP is suitable for all popular operating environments, can be used unlimitedly on Microsoft Windows, MacOS, Linux-like systems.
The protocol has essentially no disadvantages. It is somewhat more difficult to configure compared to FTP, requires greater hardware capacity, since it carries out not only the transfer, but also the encryption of information, but these disadvantages are more than compensated by security and other advantages unavailable to its predecessor.
How to set up a connection?
To appreciate all the advantages of the SFTP protocol, you need to set up the connection correctly. A responsible approach ensures that the information will be reliably protected, and outsiders will not be able to interfere with the communication session. The setup algorithm is as follows:
- Installing and configuring the server that will be involved in processing SFTP requests. You need to decide on the best program that supports a secure protocol, configure a firewall for the port through which the information will go, test the system to record and eliminate any shortcomings.
- Creating accounts. Each account must have data that can be interacted with, rights and access restrictions.
- Selecting an authentication method. The best option for SFTP is authentication using SSH keys. It involves monitoring two levels of authenticity, making it as secure as possible.
- Configuring software on the user's computer. You need to specify the IP address of the server involved, the port through which the information will go, authentication data, whether SSH keys or personal passwords, names for each user.
- Checking the stability of the connection. You need to make a test connection through the client program, make sure that all user rights and permissions are set correctly, information is transferred without losses, at a good speed.
SFTP clients
You can set up SFTP both through the functionality of the operating system and through third-party applications. The second option is considered more convenient, understandable to most users, offering maximum functions and capabilities. It is worth considering several popular applications in more detail.

FileZilla
A universal program compatible with all operating systems. SFTP setup is intuitive, on the left you can see the local device, on the left - the remote one. Copying data is initiated by simply moving between the halves of the screen.
WinSCP
Development designed for Microsoft OS. Interaction with files is also built on a structure with a pair of windows, you can set up automatic work using scripts, the level of protection meets even the most stringent requirements.
Cyberduck
An application that helps to effectively use SFTP in Microsoft Windows and MacOS. The signature advantage is synchronization with cloud services, simplifying the transfer of information.

Transmit
A special program for MacOS users. Functionality and security are at the highest levels, interaction with large data arrays is available, interfaces are simple and clear.
Summing up
SFTP is confidently in the leading group of protocols that allow exchanging information not only quickly, but also safely. It can be used and configured both using the tools built into the operating system and through third-party services. The main thing is to pay due attention to basic precautions and update the software in a timely manner.
Answers to popular questions
How soon can I start using the service?
The user account is opened immediately after the application is submitted.
Immediately after making the payment, you can start using the service immediately.